Tag: Malware
-
A Quick Look at ELF Bifrose (Part 1)
Bifrose or Bifrost is a backdoor initially targeting Windows systems with a long history. First identified in the early 2000’s, it is believed a hacking group (likely BlackTech), purchased the source code or gained access to it around 2010, and enhanced the malware for use in its own campaigns. BlackTech has long targeted both Windows…
-
Analyzing Manjusaka Infrastructure
21 August 2022 Recently, Avast tweeted a GitHub link of indicators of compromise (IOC) linked to the Manjusaka Framework. Cisco Talos released a blog earlier this month covering the framework in great detail, so I will not rehash their great work here. https://blog.talosintelligence.com/2022/08/manjusaka-offensive-framework.html Self-admittedly, I briefly glanced over the detection rules and scripts and immediately…
-

Overview of AppleSeed Dropper
02 June 2022 Summary The Kimsuky APT Group has routinely utilized the AppleSeed Backdoor to target various entities within South Korea, mainly for the purposes of espionage. While phishing still remains the primary vector of delivering the backdoor, over the past year, Kimsuky has gone to great lengths to disguise its attacks, utilizing numerous types…
-

Detecting COM Object Tasks Used by DarkHotel
Background Adversaries frequently utilize scheduled tasks, a legitimate Windows operating system utility to establish/maintain persistence and even execute code in a victim network. Scheduled tasks allow for persistence on a victim network between reboots as well as code execution when a certain condition is met (time, user logon, etc.). In this specific example, the adversary…
-

Shortcut to Windows Update
Summary On January 27, 2022, Malwarebytes Labs shared an article covering new tactics including abusing the Windows Update Client for code executing believed to be the work of Lazarus. The purpose of this post will be to cover possible detection points for defenders to identify adversaries misusing the Windows Update Client. Please give the blog…
-

Info-Stealing Tool Posing As Naver OTP
Summary SHA256: 3275f42c85c9e2fcb80d1f8c1c6227c2bcde9c0e719905ddbd2ca7373c6a8ec6 Filename: UpHelpers.exe Size: 3.41MB Extension: EXE Compilation Timestamp: 2022-01-05 23:41:20 Sandbox analysis: https://tria.ge/220118-emrgjsgfb7 UpHelpers.exe is an information-stealing/reconnaissance tool disguised as a Naver One Time Password, (OTP) generator app. Naver is a South Korean web portal that first debuted in 1999 and offers a number of services. The tool collects drive and directory…
-

Analysis of njRAT PowerPoint Macros
I wanted to do a quick write-up on an interesting PowerPoint macro document that contains njRAT. njRAT is a .NET trojan first identified in 2013 that has largely targeted countries in the Middle East as well as South America. The malicious document can be found via MalwareBazaar: https://bazaar.abuse.ch/sample/edba3ca498110106418658167533034aeb929276fe81de80c6de1a6bb95120e0 Information Gathering When triaging a suspected malicious…
-
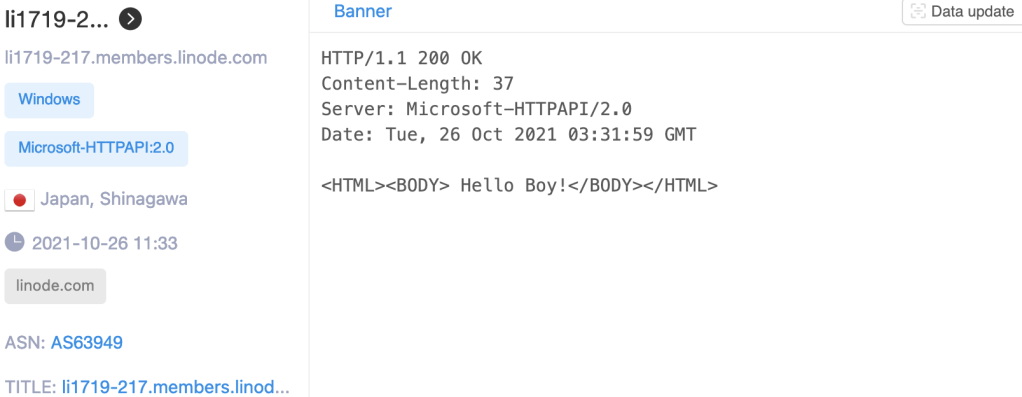
More Flagpro, More Problems
No stranger to this blog, BlackTech has continued to modify techniques to compromise networks and even suffered an OPSEC slip in the way of an open directory. This post will cover a malicious document similar to that identified by [1] PWC and [2] NTT in the previous reporting on the group. While I cannot definitively…