Bifrose or Bifrost is a backdoor initially targeting Windows systems with a long history. First identified in the early 2000’s, it is believed a hacking group (likely BlackTech), purchased the source code or gained access to it around 2010, and enhanced the malware for use in its own campaigns.
BlackTech has long targeted both Windows and Unix-based systems with a variety of malicious software, tailoring different malware to each campaign.
It Started With A Tweet
On 24 November, Twitter user @strinsert1Na tweeted that a recent ELF Bifrose sample had been uploaded to VirusTotal.

While the reuse of command and control (C&C) infrastructure is nothing new for BlackTech, the operators have consistently added new features to the backdoor, while seemingly not changing the targets of their attacks.
“udevd-10.138.61.156”
As of the time of writing, the latest Bifrose sample is detected by about half of the vendors on VirusTotal, scoring a 36 out of 64.

Although we have a good idea the file in question is an ELF file, running the file command will provide us with confirmation of the file type as well as if the file has been stripped.
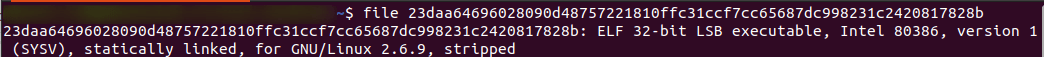
Sure enough, the output identifies the executable has been stripped; in other words, the symbols containing human-readable function names have been removed to slow down analysis.
If you’re still unsure the file is stripped, try running readelf -s filename. In this case, no output confirms the file’s symbols have been tampered with.
Running readelf with the “-p” argument on the .comment section will provide the compiler version and development environment.
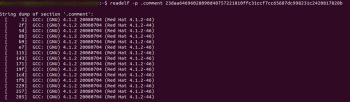
From the above output, we can infer that this sample is likely targeting Red Hat distributions.
Probably one of the best analysis tools, the strings command can assist in identifying the functionality of the executable, as well as indicators (think Windows APIs for PEs, & syscalls for Unix). The output in Figure 5 provides a small snapshot of running strings.
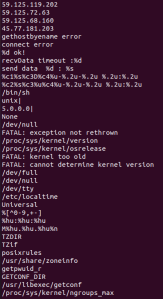
In addition to the hard-coded IP addresses, standard strings indicating first contact with the C&C server, notably unix|, 5.0.0.0|, and what appear to be C&C commands (recvData and send data), are visible in the output.
Additionally, we can see signs of reconnaissance of the infected system, viewing the version and OS release, as well as the kernel version, and the timezone the target is located in.
Bifrose Capabilities
If you don’t have Sysmon for Linux setup in a VM, or aren’t quite ready to upload the sample to a public sandbox, one great option is to utilize strace to run the sample and redirect the output to a separate file.
strace output will include operations such as any network connections or attempts, system calls, file read and write operations, etc., all information that is extremely valuable to understand the program’s behavior.
The command strace -o strace_results.txt ./elf_file is all you need, along with Wireshark, TCPDump, or any other tool that can capture network traffic. Explaining the syscalls identified in the strace output would be an article or two, and I would like to keep this short. If your interested in strace, see the below links section.
Figure 6 and 7 show snippets of interesting system calls Bifrose makes when run.


To keep things simple, we’ll use Mandiant’s CAPA tool to get an idea of what Bifrose is up to.

In the next post, I’ll use Cutter to look at some of the capabilities identified in the above image and see if we can map out the execution of Bifrose, to help defenders get an idea of what indicators will assist in identifying a possible intrusion.
Links
https://man7.org/linux/man-pages/man2/syscalls.2.html
https://www.intezer.com/blog/malware-analysis/elf-malware-analysis-101-part-3-advanced-analysis/
Comments
43 responses to “A Quick Look at ELF Bifrose (Part 1)”
[…] backdoors like KIVARS and XBOW.Linux variants of BIFROSE (aka ELF_BIFROSE) have been observed since at least 2020 with capabilities to launch remote shells, download/upload files, and perform file […]
LikeLike
[…] variants of BIFROSE (aka ELF_BIFROSE) have been observed since at least 2020 with capabilities to launch remote shells, download/upload files, and perform file […]
LikeLike
[…] variants of BIFROSE (aka ELF_BIFROSE) have been observed since at least 2020 with capabilities to launch remote shells, download/upload files, and perform file […]
LikeLike
[…] von BIFROSE, die auch als ELF_BIFROSE bezeichnet werden, wurden zur Kenntnis genommen aus mindestens 2020 die Möglichkeit haben, Remote-Shells zu starten, Dateien hoch- und herunterzuladen und […]
LikeLike
[…] A Quick Look at ELF_BIFROSE […]
LikeLike
[…] backdoors like KIVARS and XBOW.Linux variants of BIFROSE (aka ELF_BIFROSE) have been observed since at least 2020 with capabilities to launch remote shells, download/upload files, and perform file […]
LikeLike
[…] versiones Linux de BIFROSE, también conocidas como ELF_BIFROSE, han sido nota de al menos 2020 para tener la capacidad de lanzar shells remotos, cargar/descargar archivos y realizar operaciones […]
LikeLike
[…] variants of BIFROSE (aka ELF_BIFROSE) have been noticed since at the very least 2020 with capabilities to launch distant shells, obtain/add recordsdata, and carry out file […]
LikeLike
[…] variants of BIFROSE (aka ELF_BIFROSE) have been observed since at least 2020 with capabilities to launch remote shells, download/upload files, and perform file […]
LikeLike
[…] variants of BIFROSE (aka ELF_BIFROSE) have been observed since at least 2020 with capabilities to launch remote shells, download/upload files, and perform file […]
LikeLike
[…] variants of BIFROSE (aka ELF_BIFROSE) have been observed since at least 2020 with capabilities to launch remote shells, download/upload files, and perform file […]
LikeLike
[…] (diğer adıyla ELF_BIFROSE) Linux çeşitleri gözlemlendi o zamandan beri en az 2020 Uzak kabukları başlatma, dosyaları indirme/yükleme ve dosya işlemlerini gerçekleştirme […]
LikeLike
[…] variants of BIFROSE (aka ELF_BIFROSE) have been observed since at least 2020 with capabilities to launch remote shells, download/upload files, and perform file […]
LikeLike
[…] variants of BIFROSE (aka ELF_BIFROSE) have been observed since at least 2020 with capabilities to launch remote shells, download/upload files, and perform file […]
LikeLike
[…] variants of BIFROSE (also known as ELF_BIFROSE) have been noticed since at least 2020 with capabilities to launch remote shells, download/upload files, and perform file […]
LikeLike
[…] variants of BIFROSE (aka ELF_BIFROSE) have been observed since at least 2020 with capabilities to launch remote shells, download/upload files, and perform file […]
LikeLike
[…] variants of BIFROSE (aka ELF_BIFROSE) have been observed since at least 2020 with capabilities to launch remote shells, download/upload files, and perform file […]
LikeLike
[…] han publicado variantes de Linux de BIFROSE (también conocido como ELF_BIFROSE). observado desde al menos 2020 con capacidades para iniciar shells remotos, descargar/cargar archivos y realizar operaciones con […]
LikeLike
[…] Linux variants of BIFROSE, also known as ELF_BIFROSE, have been identified with abilities like launching remote shells, file downloads/uploads, and file manipulation since at least 2020. […]
LikeLike
[…] variantes Linux de BIFROSE (alias ELF_BIFROSE) ont été observé depuis au moins 2020 avec des capacités pour lancer des shells distants, télécharger/télécharger des fichiers et […]
LikeLike
[…] variants of BIFROSE (aka ELF_BIFROSE) have been observed since at least 2020 with capabilities to launch remote shells, download/upload files, and perform file […]
LikeLike
[…] di BIFROSE per Linux (detto anche ELF_BIFROSE) sono state osservate almeno dal 2020, con capacità di lanciare shell remote, scaricare/caricare file e eseguire operazioni sui […]
LikeLike
[…] variants of BIFROSE (aka ELF_BIFROSE) have been observed since at least 2020 with capabilities to launch remote shells, download/upload files, and perform file […]
LikeLike
[…] di BIFROSE per Linux (detto anche ELF_BIFROSE) sono state osservate almeno dal 2020, con capacità di lanciare shell remote, scaricare/caricare file e eseguire operazioni sui […]
LikeLike
[…] variants of BIFROSE (aka ELF_BIFROSE) have been observed since at least 2020 with capabilities to launch remote shells, download/upload files, and perform file […]
LikeLike
[…] variants of BIFROSE (aka ELF_BIFROSE) have been observed since at least 2020 with capabilities to launch distant shells, obtain/add recordsdata, and carry out file […]
LikeLike
[…] variants of BIFROSE (aka ELF_BIFROSE) have been observed since at least 2020 with capabilities to launch remote shells, download/upload files, and perform file […]
LikeLike
[…] versions Linux de BIFROSE, également appelées ELF_BIFROSE, ont été noté de au moins 2020 d’avoir la capacité de lancer des shells à distance, de télécharger des fichiers et […]
LikeLike
[…] variants of BIFROSE (aka ELF_BIFROSE) have been observed since at least 2020 with capabilities to launch remote shells, download/upload files, and perform file […]
LikeLike
[…] han publicado variantes de Linux de BIFROSE (también conocido como ELF_BIFROSE). observado desde al menos 2020 con capacidades para iniciar shells remotos, descargar/cargar archivos y realizar operaciones con […]
LikeLike
[…] variants of BIFROSE (aka ELF_BIFROSE) have been observed since at least 2020 with capabilities to launch remote shells, download/upload files, and perform file […]
LikeLike
[…] variants of BIFROSE (aka ELF_BIFROSE) have been observed since at least 2020 with capabilities to launch remote shells, download/upload files, and perform file […]
LikeLike
[…] variants of BIFROSE (aka ELF_BIFROSE) have been observed since at least 2020 with capabilities to launch remote shells, download/upload files, and perform file […]
LikeLike
[…] variants of BIFROSE (aka ELF_BIFROSE) have been observed since at least 2020 with capabilities to launch remote shells, download/upload files, and perform file […]
LikeLike
[…] variants of BIFROSE (aka ELF_BIFROSE) have been observed since at least 2020 with capabilities to launch remote shells, download/upload files, and perform file […]
LikeLike
[…] variants of BIFROSE (aka ELF_BIFROSE) have been observed since at least 2020 with capabilities to launch remote shells, download/upload files, and perform file […]
LikeLike
[…] variants of BIFROSE (aka ELF_BIFROSE) have been observed since at least 2020 with capabilities to launch remote shells, download/upload files, and perform file […]
LikeLike
[…] variants of BIFROSE (aka ELF_BIFROSE) have been observed since at least 2020 with capabilities to launch remote shells, download/upload files, and perform file […]
LikeLike
[…] variants of BIFROSE (aka ELF_BIFROSE) have been observed since at least 2020 with capabilities to launch remote shells, download/upload files, and perform file […]
LikeLike
[…] variants of BIFROSE (aka ELF_BIFROSE) have been observed since at least 2020 with capabilities to launch remote shells, download/upload files, and perform file […]
LikeLike
[…] variants of BIFROSE (aka ELF_BIFROSE) have been observed since at least 2020 with capabilities to launch remote shells, download/upload files, and perform file […]
LikeLike
[…] Linux versions of BIFROSE, also referred to as ELF_BIFROSE, have been noted from at least 2020 to have the ability to launch remote shells, upload/download files and conduct file […]
LikeLike
[…] Mike at “CyberSec & Ramen”A Quick Look at ELF Bifrose (Part 1) […]
LikeLike